What You Can Do
With Azure DevOps connected, Overcut agents can:- Access Repositories: Clone, read, and modify code in your Azure DevOps repositories
- Manage Work Items: Create, update, and comment on Azure DevOps work items (bugs, tasks, user stories)
- Handle Pull Requests: Review, comment on, and manage pull requests
- Code Operations: Clone repositories, create branches, and perform git operations
- Webhook Triggers: Automatically start workflows based on Azure DevOps events
- Repository Configuration: Configure agent behavior per repository
Prerequisites
- An Azure DevOps organization with access to repositories you want to connect
- Azure Active Directory (Entra ID) admin permissions to grant application consent
- Project Administrator permissions in Azure DevOps projects where you want webhook integration
- An active Overcut workspace
Setup Overview
Azure DevOps integration uses a service principal (application identity) that operates on behalf of your organization. This approach provides: Service Principal Advantages:- Consistent Bot Identity: All operations appear under a single, recognizable application identity
- Enterprise Security: Centralized permission management through Azure Active Directory
- Independence: Integration survives team member departures and role changes
- Clear Attribution: Team members know which actions were automated vs. manual
- Scalable Management: Single identity works across all projects and repositories
- Token Stability: Authentication remains valid regardless of personnel changes
Setup Steps
Grant Admin Consent in Azure Active Directory
An Azure AD admin must grant consent for Overcut to access your Azure DevOps organization.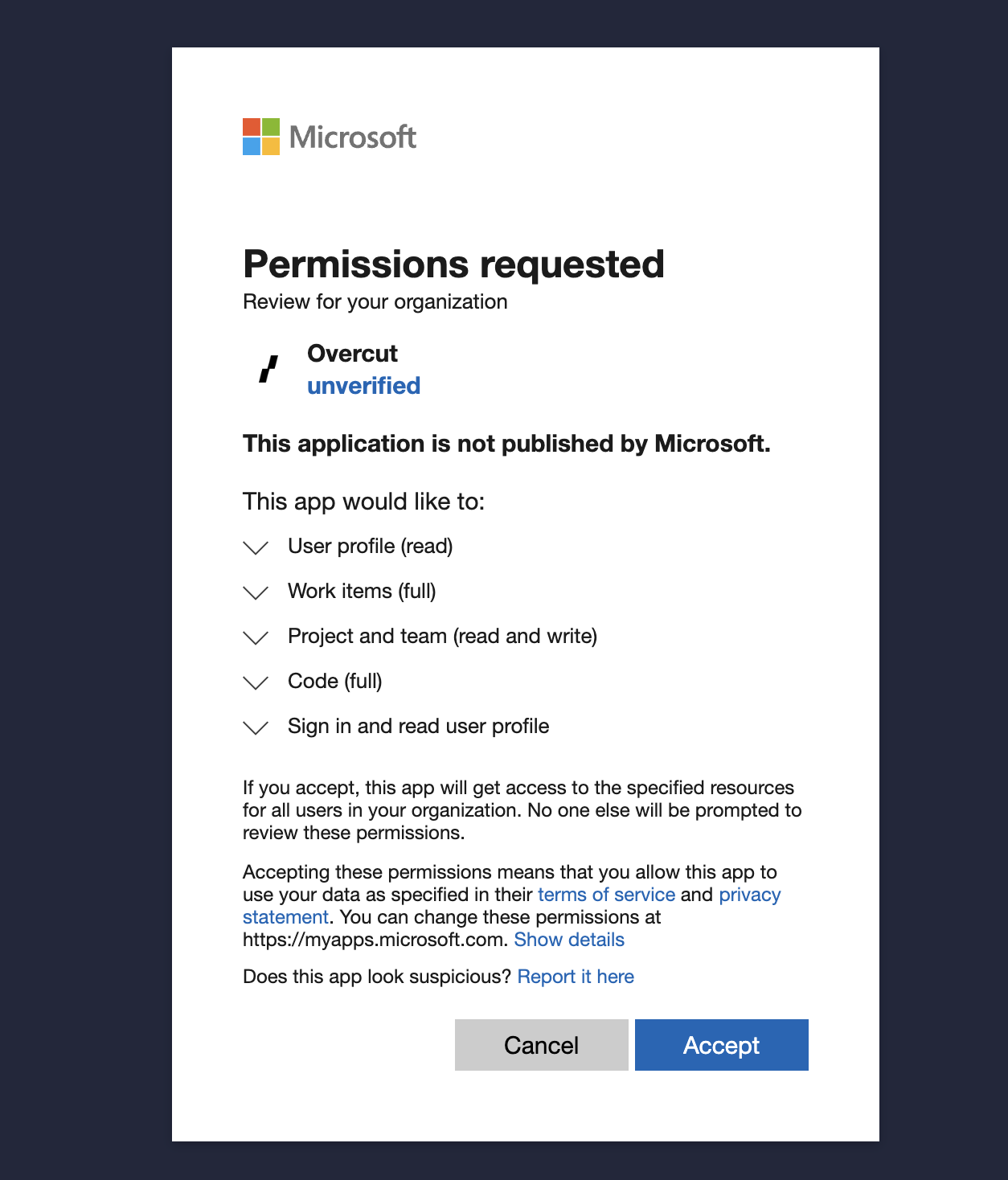
Admin Consent Process:

- In your Overcut workspace, go to Integrations
- Click Connect Azure DevOps
- Enter your Azure DevOps organization name when prompted
- You’ll be redirected to Microsoft’s admin consent page
- Sign in as an Azure AD administrator for your tenant
- Review the requested permissions:
- Azure DevOps API access for repositories, work items, and webhooks
- Microsoft Graph access for tenant validation
- Grant consent for the entire organization
- Complete the authorization flow
Only Azure AD administrators can grant tenant-wide consent. If you’re not an admin, you’ll need to coordinate with your IT team for this step.
Add Service Principal to Azure DevOps
The service principal must be manually added to your Azure DevOps organization and granted appropriate permissions.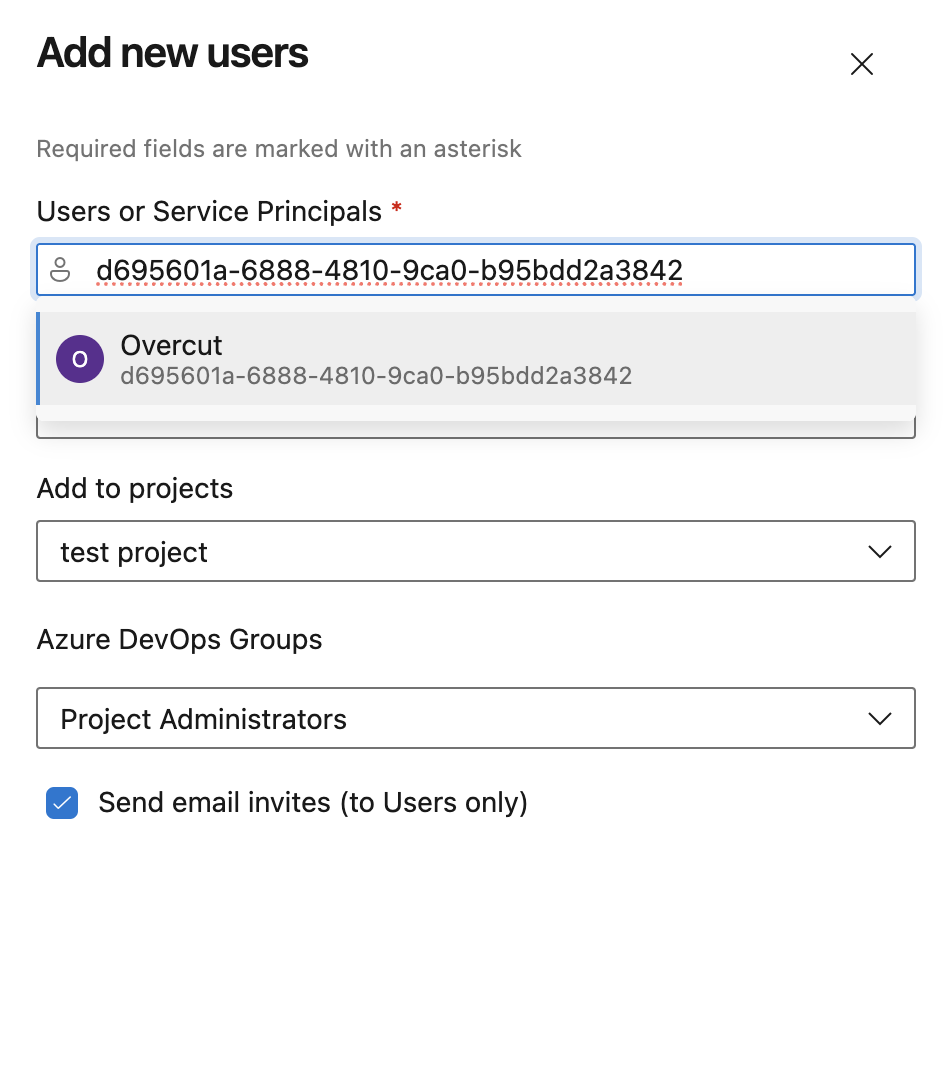
Add to Organization:

-
Navigate to Azure DevOps Organization Settings:
- Go to
https://dev.azure.com/{your-org}/_settings/users
- Go to
-
Add the Service Principal as a User:
- Click Add users
- User or Service Principal: search for
d695601a-6888-4810-9ca0-b95bdd2a3842(Overcut App client ID) - Access Level: Select
Basic(minimum required for full functionality) - Add to projects: select the project(s) you want to add the service principal to
- Azure DevOps Groups: select
Project Administrators - Click Add
Complete Integration in Overcut
Return to Overcut to finalize the connection. Once the service principal is added to the Project Administrators group, you need to run the same flow again to complete the integration.
- After granting admin consent, you’ll be redirected back to Overcut
- Overcut will detect the service principal and complete the integration setup
- Verify the connection by checking that your Azure DevOps projects appear in the provider list
- Add repositories from your Azure DevOps projects.
Permissions
The Azure DevOps integration uses the following permissions:Azure DevOps API Access
- Full API Access: Comprehensive access to Azure DevOps services including:
- Repository Operations: Read and write repository contents, create branches, manage pull requests
- Work Item Management: Create, read, update work items (bugs, tasks, user stories, etc.)
- Webhook Management: Create and manage service hooks for event notifications
- Project Access: Access to project and organization information
Next Steps
After connecting Azure DevOps:- Explore repository configuration options for fine-tuned agent behavior
- Set up workflow triggers to respond to Azure DevOps events
- Create workflows that leverage both code and work item operations
- Monitor agent activity through Azure DevOps audit logs